In this article we will demonstrate how we can leverage Azure Key Vault for managing SSH keys to access our Azure Virtual Machines. It is always a challenge as to how we manage secure information especially private keys, with this approach we can leverage Azure Key Vault to securely store this information. We will be performing the tasks using Azure CLI 2.0 (a primer can be found here).

Azure Key Vaults allow us to securely store sensitive information such as keys and passwords. We do this by creating secure containers named “Vaults” that we can use to assign access to for our applications. You can extend this process to use your own CA or sign certificates with a public CA, however we will use self-signed certificates in this article.
You would generally use Key Vault for various purposes, especially for delivering certificates for web servers etc that can be automated. In this article we are simply solving the challenge of distributing private keys as we can leverage Key Vault to give individual users access to various secrets/keys in our vault.
Firstly (assuming we’ve fired up the CLI), we need to register the KeyVault namespace:
az provider register -n Microsoft.KeyVault
Now we need to create a resource group and a vault to store our keys. We will name the RG “rg-austeast-keystore1” and the vault “keystore1Vault1”
az group create -n rg-austeast-keystore1 -l australiaeast az keyvault create -n keystore1Vault1 -g rg-austeast-keystore1 -l australiaeast --enabled-for-deployment
Now that the Vault is created, let’s create a certificate:
az keyvault certificate create --vault-name keystore1Vault1 -n cert1 -p "$(az keyvault certificate get-default-policy -o json)"
We will need the certificate to SSH into our machine, let’s download the key and convert the private key as we are using Linux to connect to our VM (removing the password from the key):
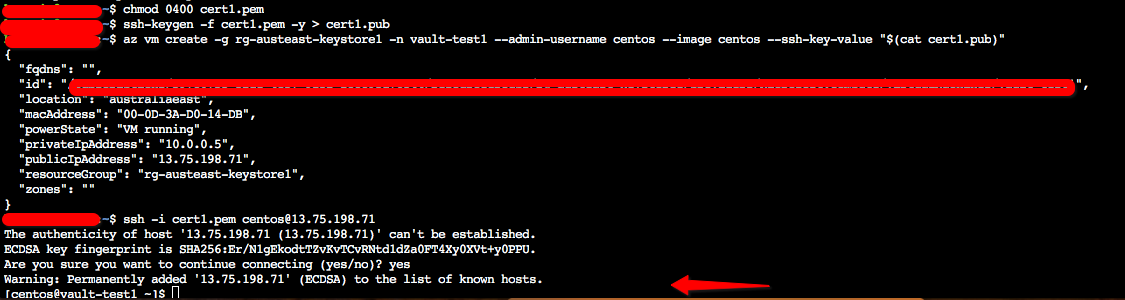
az keyvault secret download --vault-name keystore1Vault1 -n cert1 -e base64 -f cert1.pfx openssl pkcs12 -in cert1.pfx -out cert1.pem -nocerts -nodes chmod 0400 cert1.pem ssh-keygen -f cert1.pem -y > cert1.pub
Now we are ready to deploy our VM using the SSH key above above:
az vm create -g rg-austeast-keystore1 -n vault-test1 --admin-username centos --image centos --ssh-key-value "$(cat cert1.pub)"
The above will instantiate the VM for us with the required key for us to log in using the Key Vault key instantiated above. We can now test it by logging into the VM using the private key we downloaded earlier: